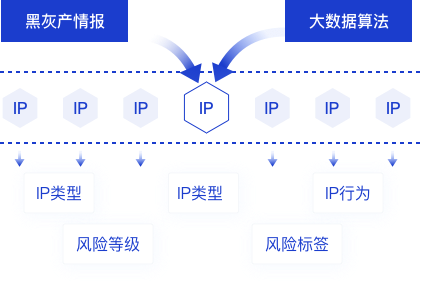
As the most basic identity in the Internet space, IP has always been the most fierce attack and defense point for the black market and Party A. In order to bypass the risk control strategy, the black market uses a large number of proxy services and PPPoE technology to frequently change IP for batch malicious activities, which has become the normal behavior of the black market. Since IP is a public resource, rashly blocking abnormal IP may damage the experience of normal users. Thus the response of risk control defense lags behind and the efficiency and effect are greatly reduced. In addition, with the popularization and application of IPv6, the black market also uses IPv6 as the underlying resource, and occupies a dominant position in the security confrontation of Internet business by virtue of the huge number of IPv6

