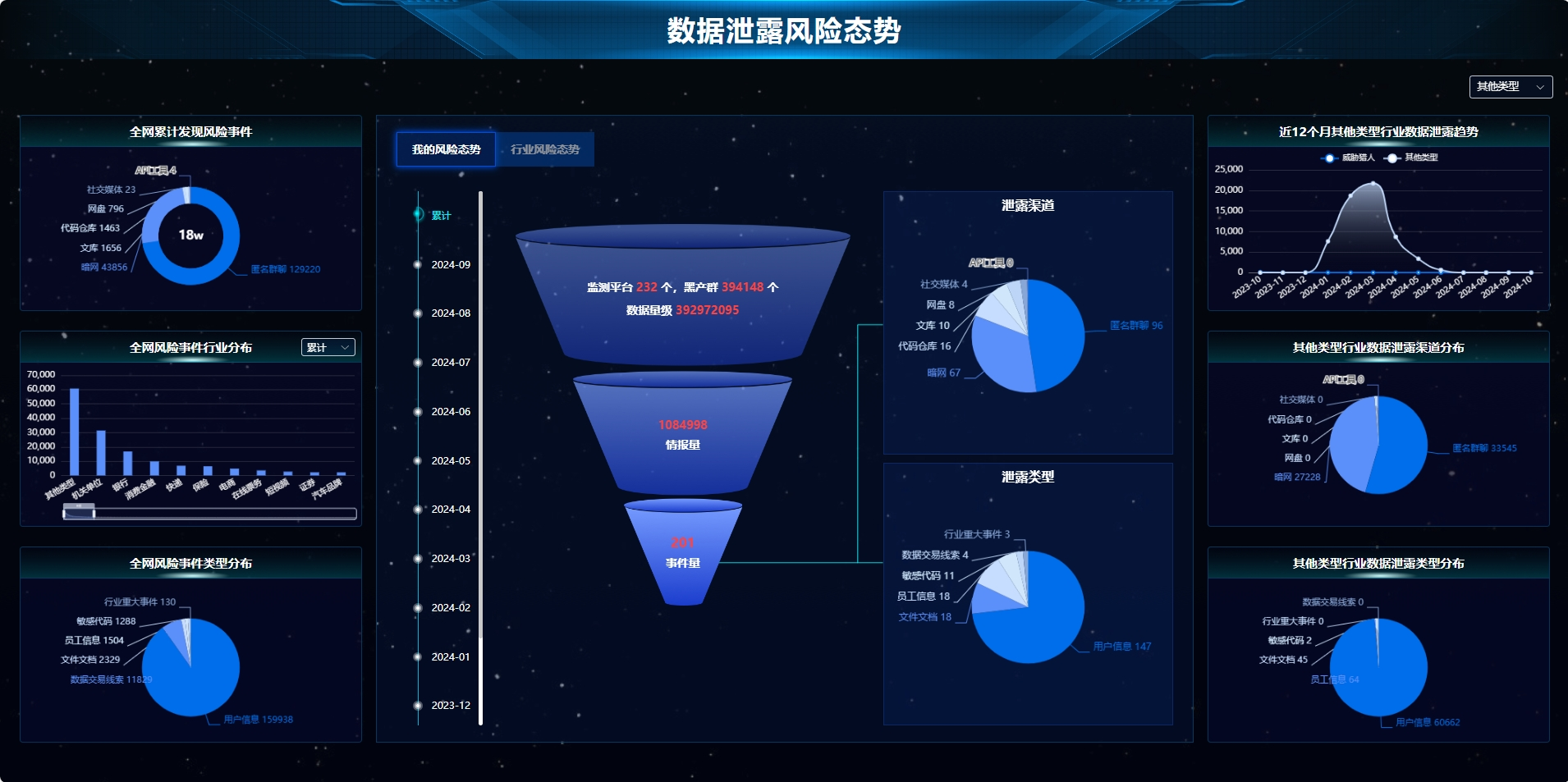
In recent years, large-scale data leakage events have occurred frequently at home and abroad, and data has become an important factor of production. All government and enterprise organizations attach increasing importance to data. The existing security construction of government and enterprise organizations generally focuses on internal detection and defense, often neglects the security situation of the external data, and fails to quickly perceive the event when the data leakage event occurs, resulting in the damage to the images of government and enterprise organizations or economic losses.
Threat Hunter data asset leakage risk monitoring platform realizes alert and concurrent validation of data in the first time through real-time monitoring of data asset leakage information of major darknets, netdisk libraries, code hosting, group chat forums and other channels, in combination with artificial intelligence analysis technology. After locating the risk, it provides traceability services to cooperate with enterprise investigation and helps customers find, accurately locate and effectively solve the data asset leakage problem, minimizes the risk and damage caused by data asset leakage and helps enterprises achieve data compliance.