Product Introduction
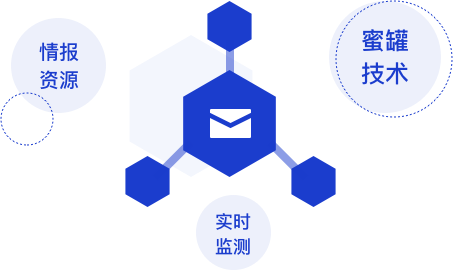
Threat Hunter mailbox risk profile is based on the unique ‘honeypot’ proxy servers technology of Ever. Security and the risk mailbox identification engine modeled by intelligence resources, and it builds a real-time monitoring system for black market gangs, helps enterprises accurately identify temporary mailboxes and various normal mailbox accounts held by black market at home and abroad, and effectively helps enterprises solve the risk problem of mailbox accounts.