Product Introduction
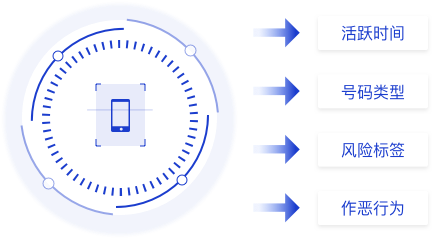
Based on Threat Hunter's unique honeypot technology and black market intelligence system, Threat Hunter mobile phone number risk profile fully analyzes the behavior and attributes of mobile phone numbers, comprehensively evaluates the risk categories of mobile phone numbers, and accurately assigns the corresponding risk tags to mobile phone numbers, which can effectively help the platform reduce the risk of business fraud.